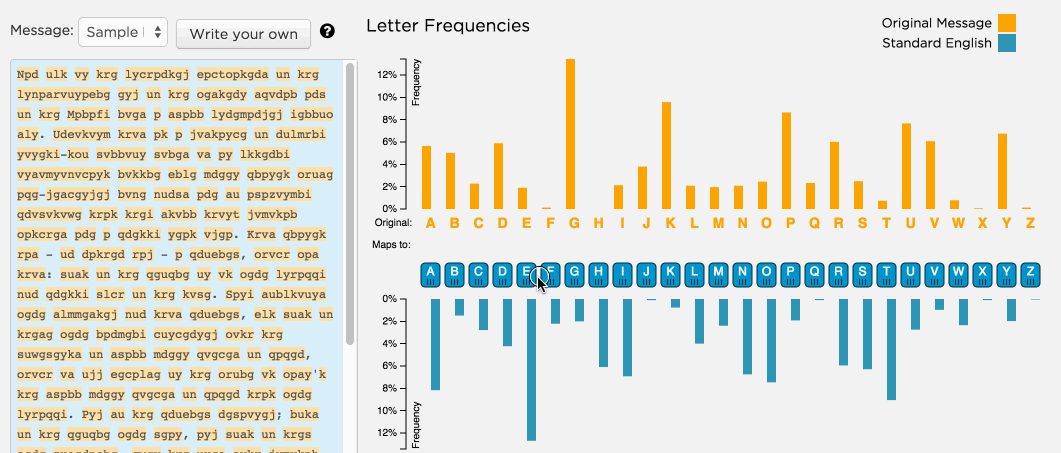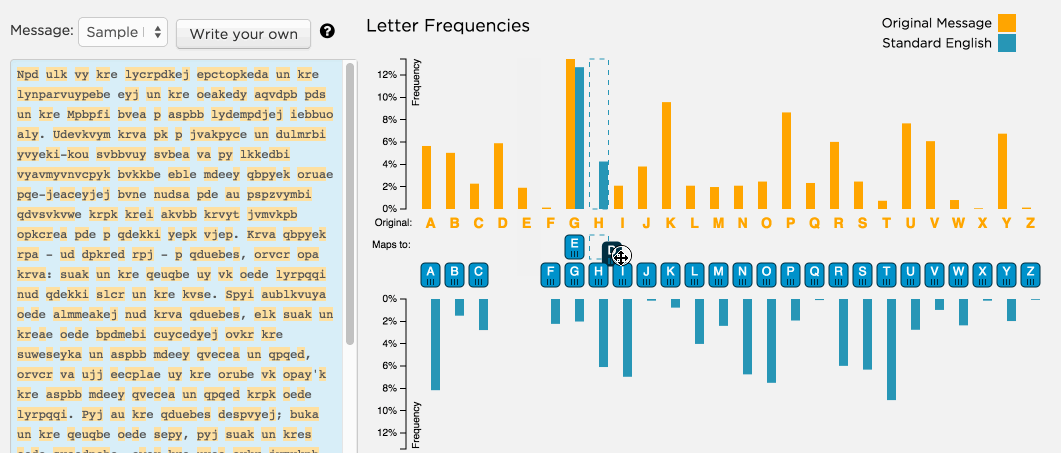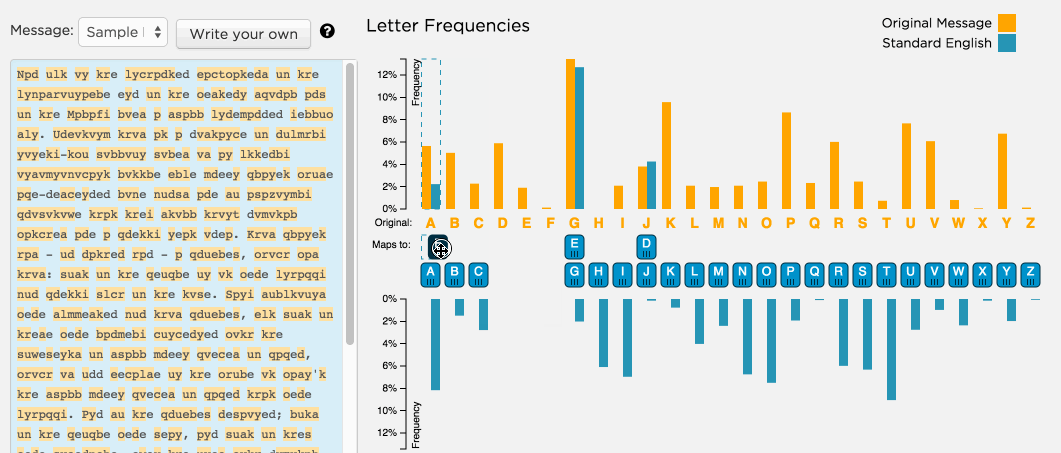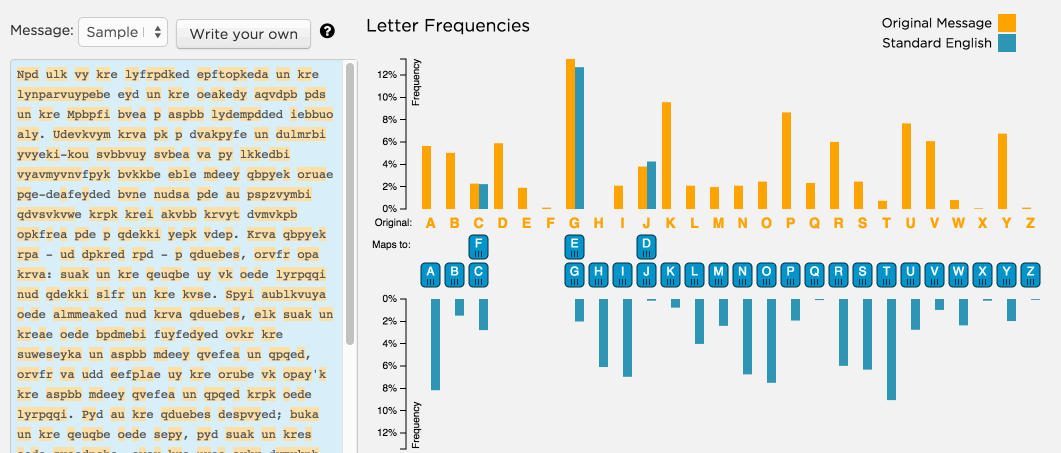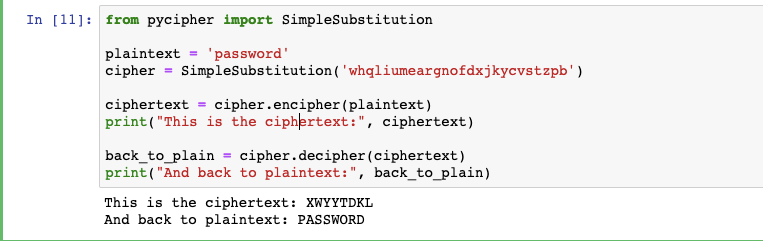
Breaking My Little Pony: Frequency Analysis for Breaking Ciphers | by Jonathan Keller | Towards Data Science
Cryptography | Free Full-Text | E-ART: A New Encryption Algorithm Based on the Reflection of Binary Search Tree | HTML
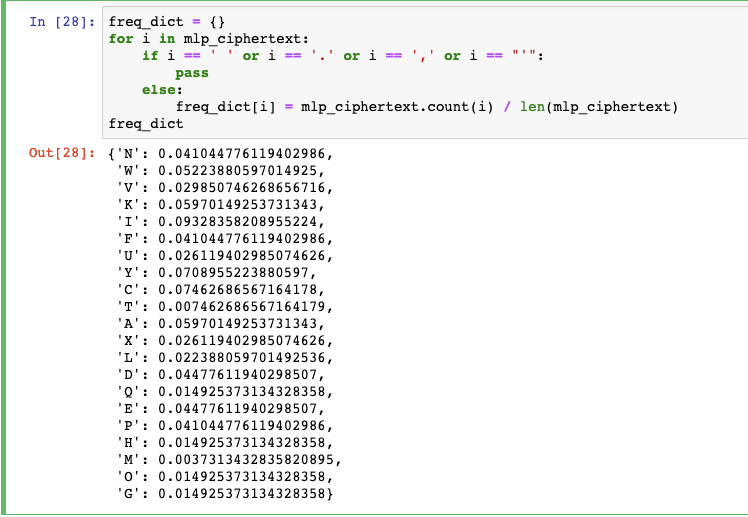
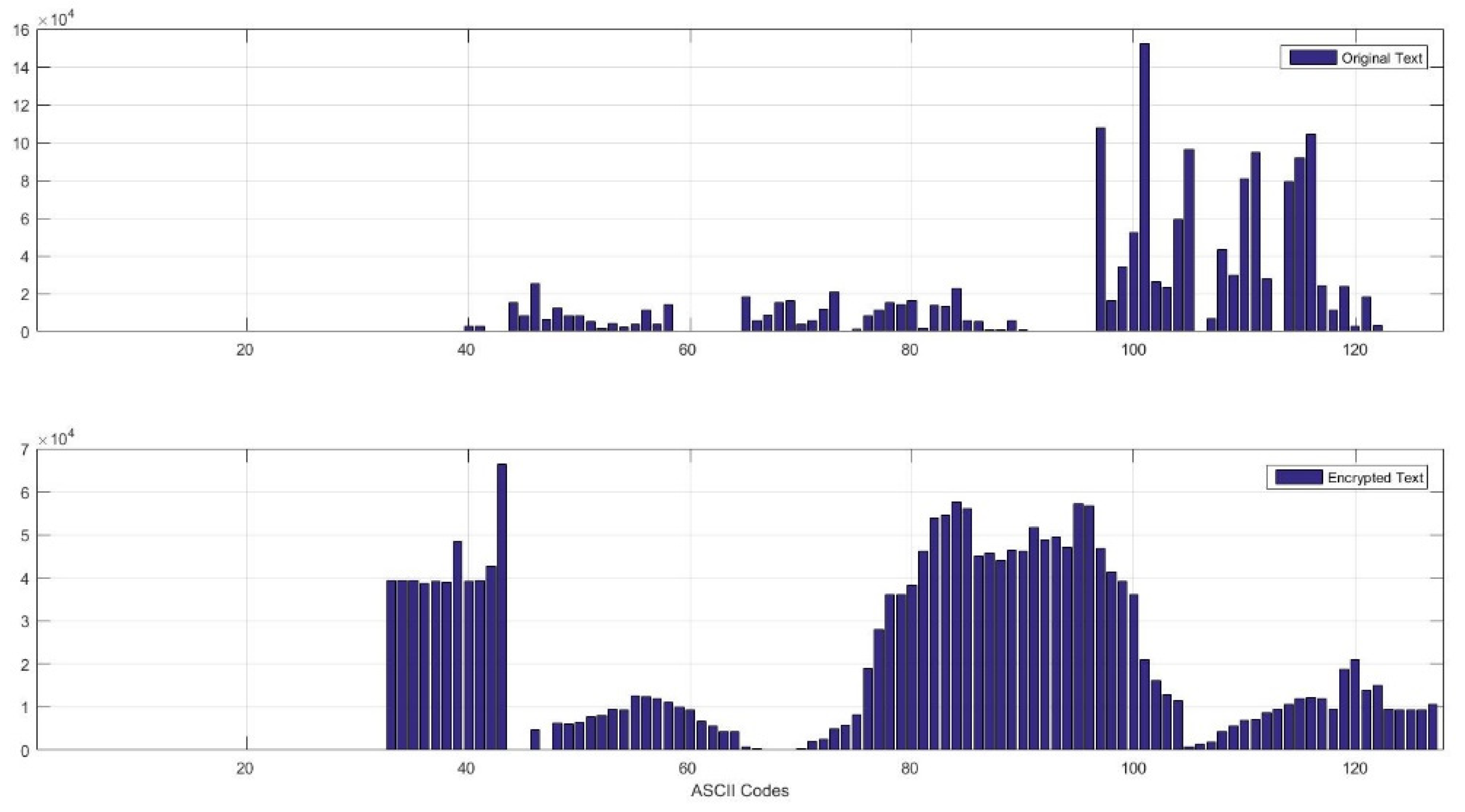
Breaking My Little Pony: Frequency Analysis for Breaking Ciphers | by Jonathan Keller | Towards Data Science

Graphical representation of Frequency Analysis Proposed Cipher with... | Download Scientific Diagram

Finding Probable Frequency Sums to Reduce the Key Space of Homophonic Substitution Ciphers — Journal of Young Investigators

Monitoring data encryption method for howitzer shell transfer arm using chaos and compressive sensing - Xi Liu, Baolin Hou, Qiangqiang Zhao, 2019