A Unified Model of Depression: Integrating Clinical, Cognitive, Biological, and Evolutionary Perspectives - Aaron T. Beck, Keith Bredemeier, 2016
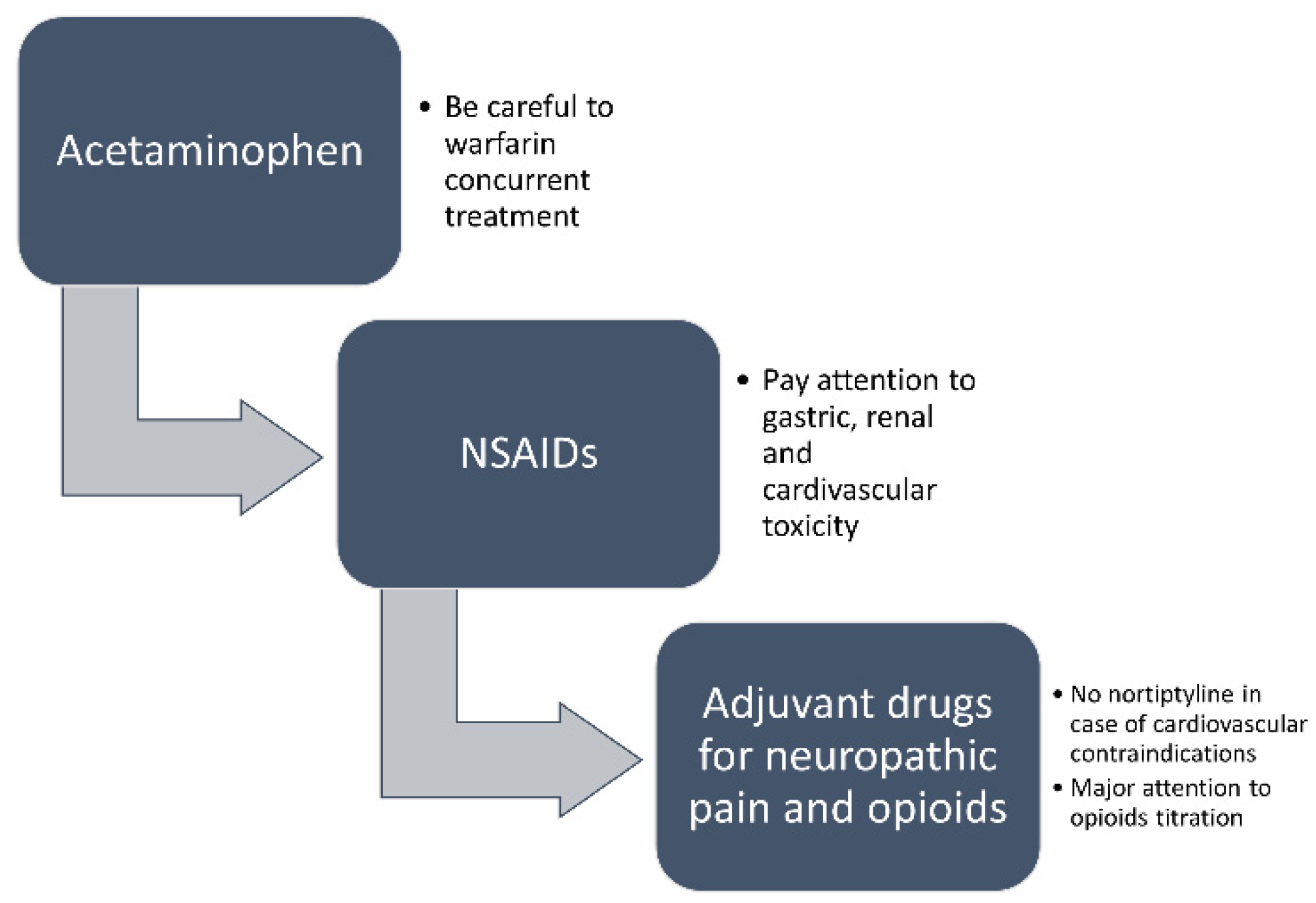
Brain Sciences | Free Full-Text | Pharmacological Treatment of Pain and Agitation in Severe Dementia and Responsiveness to Change of the Italian Mobilization–Observation–Behavior–Intensity–Dementia (I-MOBID2) Pain Scale: Study ...
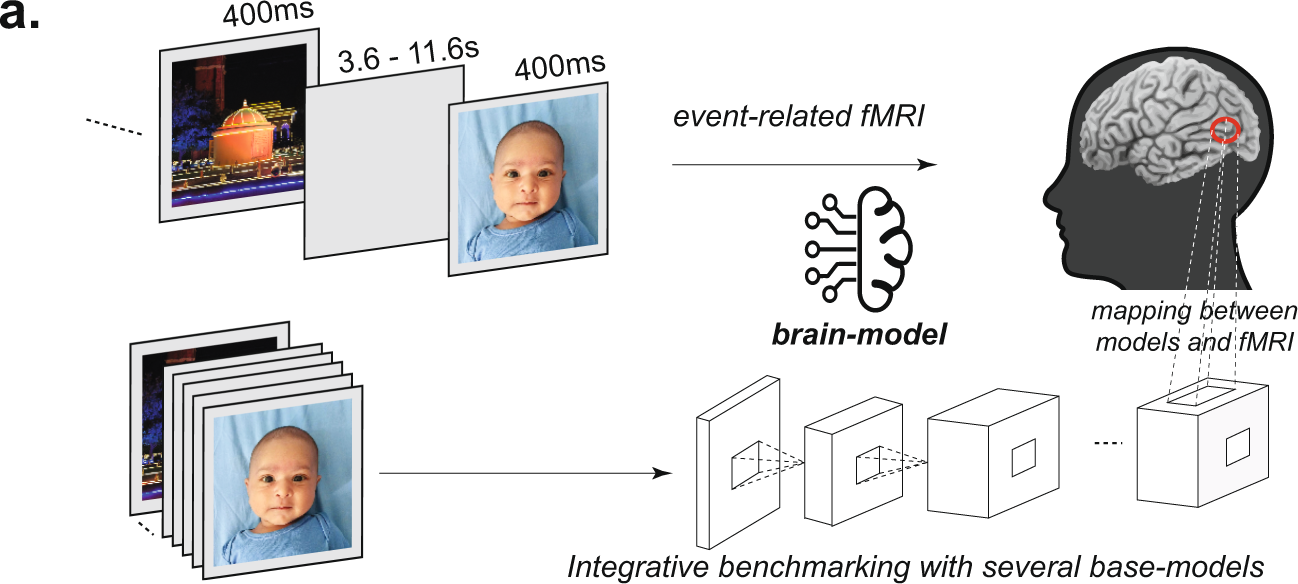
Computational models of category-selective brain regions enable high-throughput tests of selectivity | Nature Communications

CYBERSECURITY BRAINSTORM - Tech and cyber specialists are not empowered to secure cyber-systems, because device vendors are working in solo